Enterprise Network Security
A firewall and intricate password requirements no longer serve as a network security strategy. An unfortunate reality of today’s interconnected world is that company and customer data, as well as your intellectual property, are at risk 24/7. To stay ahead of these threats organizations demand that their enterprise network anticipate threats, monitor for intrusions or problems and enforce multi-layered security policy from the data center to the farthest edge; even to the end user device.
Enterprise Network Security
A firewall and intricate password requirements no longer serve as a network security strategy.
An unfortunate reality of today’s interconnected world is that company and customer data, as well as your intellectual property, are at risk 24/7. To stay ahead of these threats organizations demand that their enterprise network anticipate threats, monitor for intrusions or problems and enforce multi-layered security policy from the data center to the farthest edge; even to the end user device.
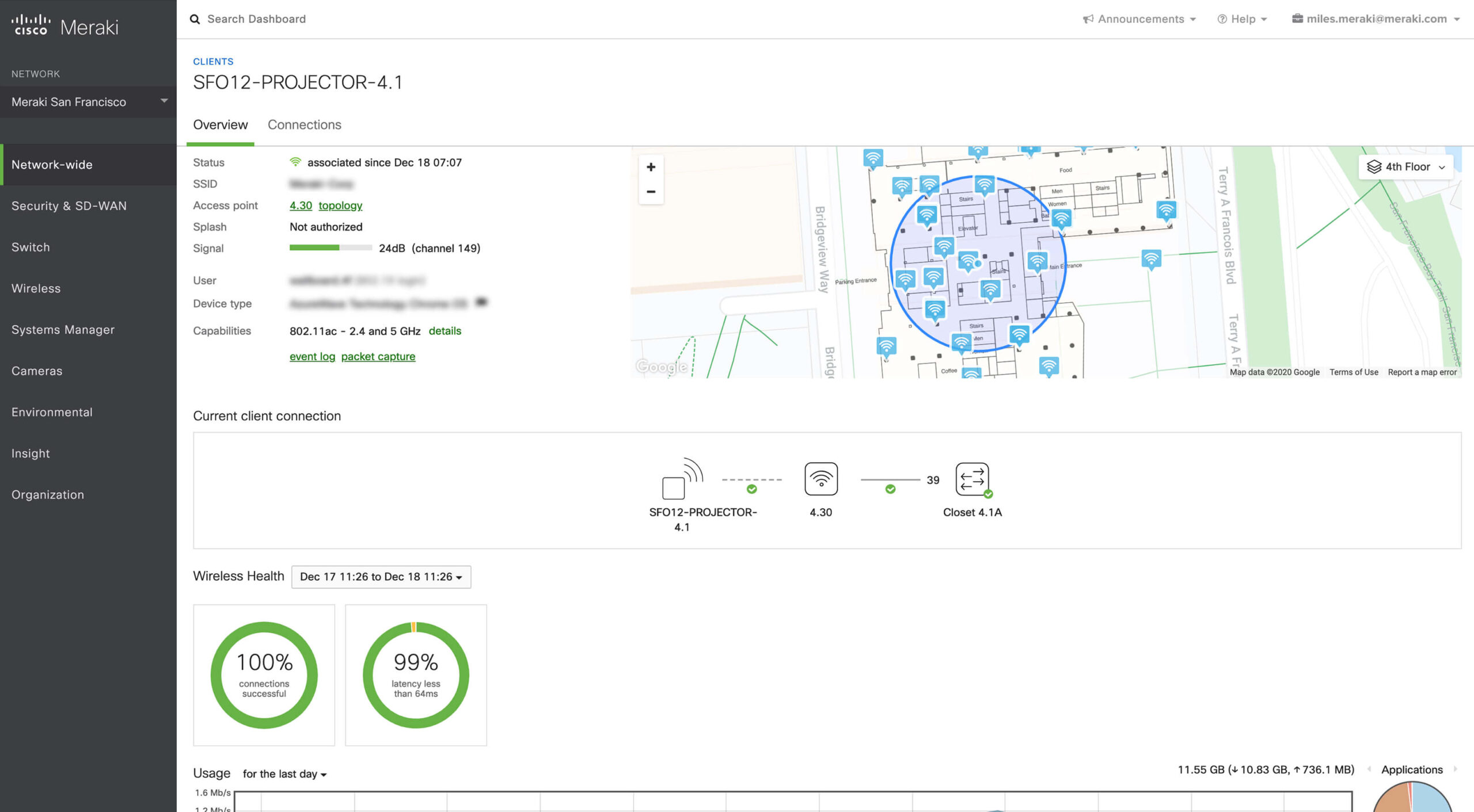

ScanOnline assists clients in assessing and developing a comprehensive security posture necessary to ensure risk mitigation and business continuity. We have a diverse portfolio of security solutions and service offerings that empower our clients to “take back the network”.
Ranging from application granularity for individual employee endpoints to applications that allow aggregation and notification of security events, there is something for every situation.
In a world that becomes more unpredictable every day, ScanOnline’s security options, from physical appliances to software monitoring tools and services lock down mission-critical information and communication important to the business.
Plus with ScanOnline’s managed services group as an optional resource, 24/7 proactive monitoring, management and maintenance is discretely taken off the plate of your IT team.

Security and Management – What We Do
- Next Generation Firewalls
- Granular Control, Context-Aware Protection by Application, User, Device and Location
- Stealth Networking
- Federation and SSO
- Virtual Service Networks and Hyper Segmentation
- 24/7 Monitoring
- Identification, Mitigation and Reporting
- Automated Compliance and Policy Enforcement
- Mobile Device Management
- Network Managed Services Available


